Community PostgreSQL is great. It isn’t built for regulated workloads out of the box. PGEE (CYBERTEC PostgreSQL Enterprise Edition) keeps the PostgreSQL you know and adds Transparent Data Encryption (TDE), stored-procedure/code encryption, enterprise-class auditing, data masking, and hardened ops tooling. That’s why it’s a better base for PDPL (Saudi Personal Data Protection Law) programs
Why PGEE over community PostgreSQL (security & compliance angle)
- Encrypts by default: TDE for data files, temp files, backups, and even encrypted replication.
- Protects code: stored procedure encryption so business logic isn’t readable in prod/backups.
- Auditing & masking: built-in tools for durable audit trails and policy-based data masking/obfuscation.
Mapping this to PDPL expectations (what the law actually pushes you to do)
- Appropriate technical/organizational measures → Full-disk DB encryption, TLS in transit, access control, and auditable logs.
- Breach handling → Have procedures and notify SDAIA within 72 hours if risk exists, and notify data subjects without undue delay.
- Records & transparency → Keep records of processing activities; disclose transfers outside KSA; data minimization & retention limits.
Legal note: this is operational guidance, not legal advice. PDPL compliance is about your whole program (people/process/tech), not just a database.
Fast install — PGEE demo on RHEL/Rocky 8/9 (encrypted from day one)
1) Disable distro PostgreSQL module (avoid conflicts)
sudo dnf module disable -y postgresql
2) Add the PGEE demo repo (example uses v16; 15/16/17 available)
for this propose i will use version 16
version=16 # available: 13 14 15 16 17
# RedHat/CentOS
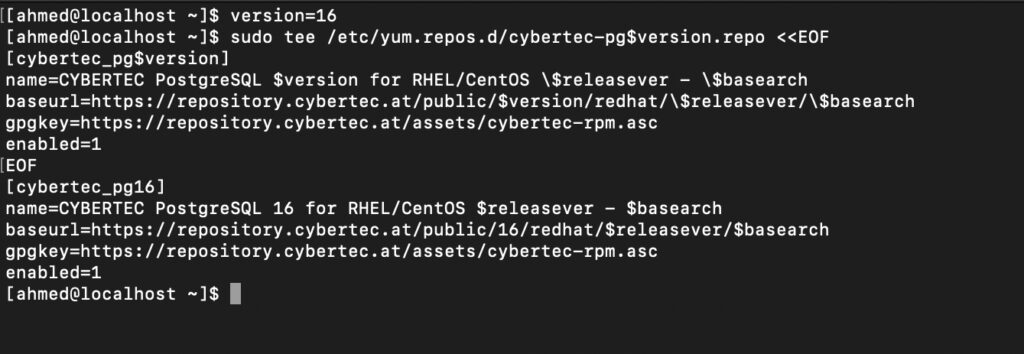
sudo tee /etc/yum.repos.d/cybertec-pg$version.repo <<EOF
[cybertec_pg$version]
name=CYBERTEC PostgreSQL $version for RHEL/CentOS \$releasever - \$basearch
baseurl=https://repository.cybertec.at/public/$version/redhat/\$releasever/\$basearch
gpgkey=https://repository.cybertec.at/assets/cybertec-rpm.asc
enabled=1
EOF
note for the demo version maximum table size allowed is 1GB
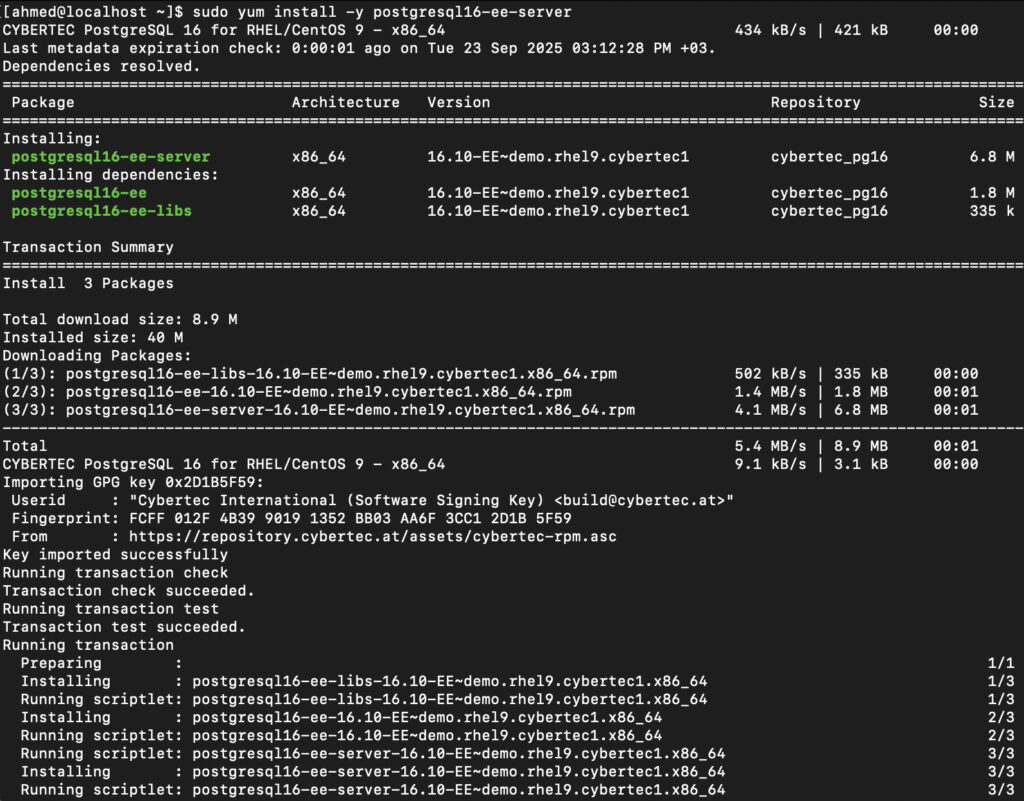
3) Install the server
sudo yum install -y postgresql16-ee-server # adjust for version
4) Initialize an encrypted cluster (TDE)
For demonstration purposes, we will initialize a database cluster with Transparent Data Encryption (TDE) to showcase the strength of Cybertec PGEE. Its TDE implementation is more advanced and capable than any alternative in the market, making it the most reliable choice for running highly sensitive operations with guaranteed data protection at rest.
# quick demo key — use CYBERTEC key manager in prod
sudo -u postgres bash -lc 'KEY=$(openssl rand -hex 16); \
/usr/pgsql-16/bin/initdb -D /var/lib/pgsql/'"$version"'/data -k -K "echo $KEY"'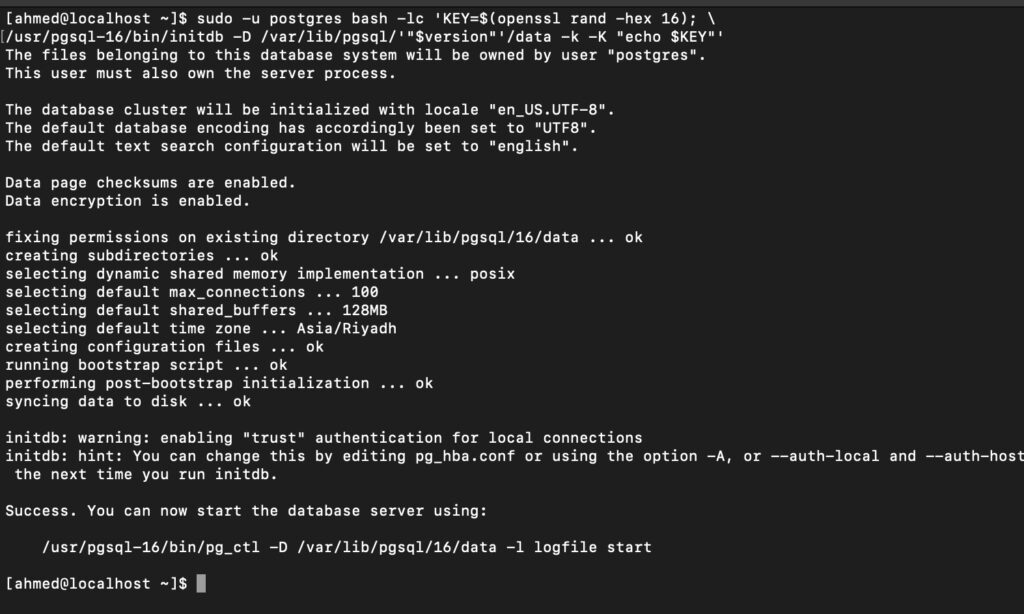
now start pgee by running the below command
systemctl start postgresql-16.service 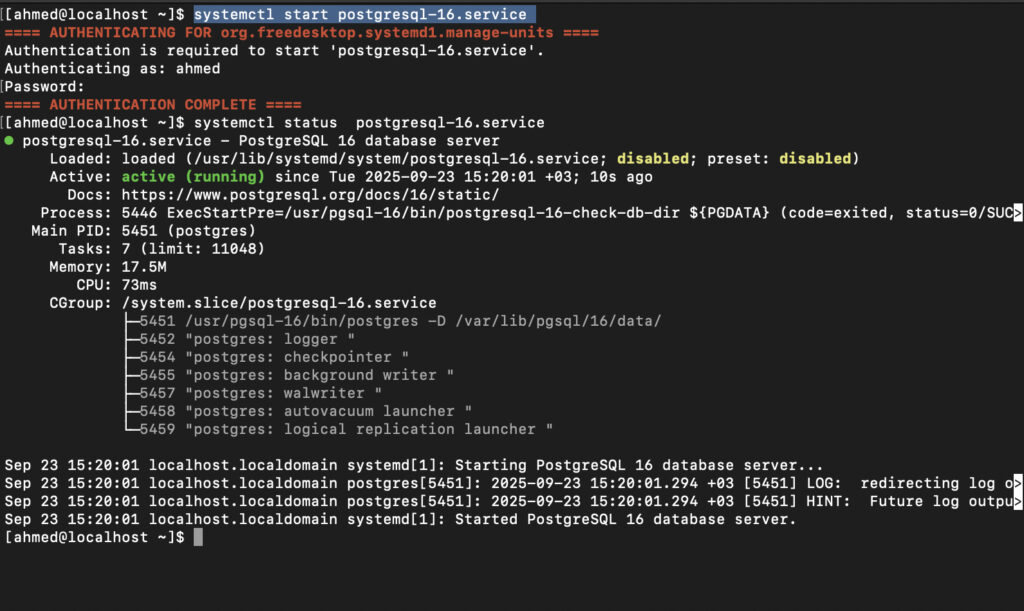
Testing and checking TDE on PGEE
Now we have successfully installed demo version of PGEE with TDE encryption .
to verify that TDE encryption is enabled login to psql and run below command , the result should return “ON”
show data_encryption;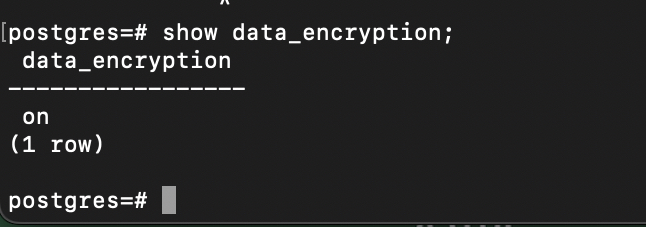
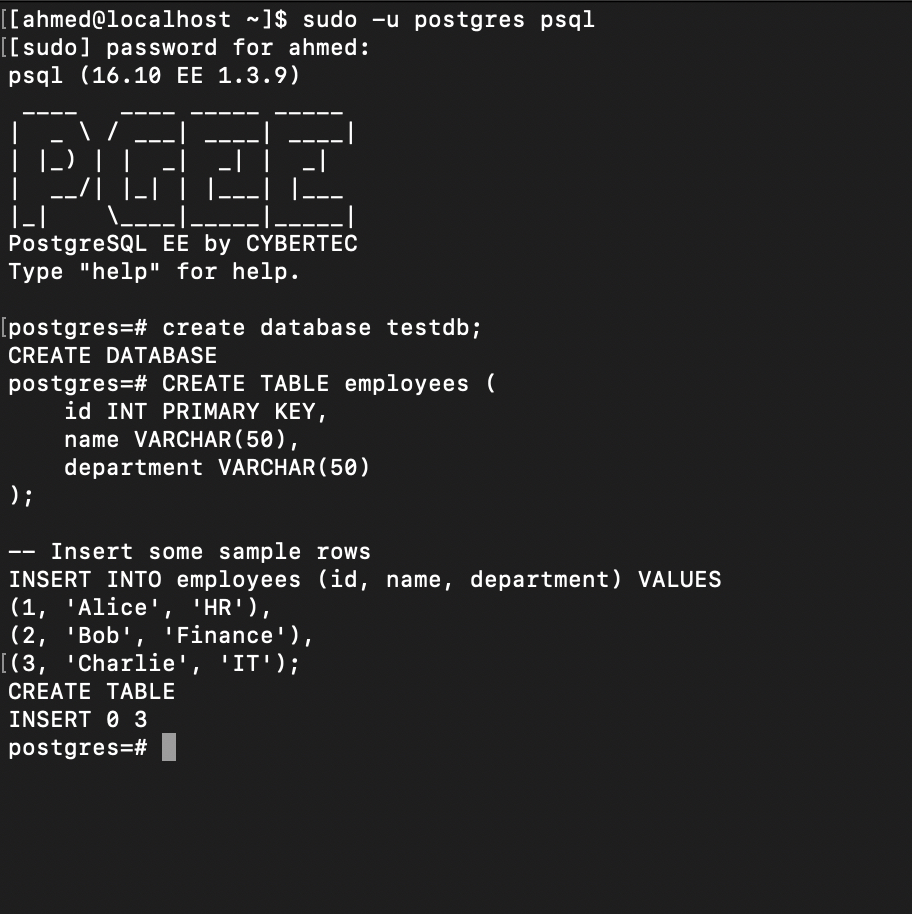
Next, we will create a sample database with a table that stores randomly generated records. This will demonstrate that if someone attempts to read the raw files directly from disk, the data remains inaccessible thanks to Transparent Data Encryption. Let’s begin by creating the database and inserting sample data into the table
Creat Database Testdb;
-- Create a simple table
CREATE TABLE employees (
id INT PRIMARY KEY,
name VARCHAR(50),
department VARCHAR(50)
);
-- Insert some sample rows
INSERT INTO employees (id, name, department) VALUES
(1, 'Alice', 'HR'),
(2, 'Bob', 'Finance'),
(3, 'Charlie', 'IT');
now lets locare where yable is located by runinng this command and then we will try to read from the disk
select pg_relation_filepath('employees');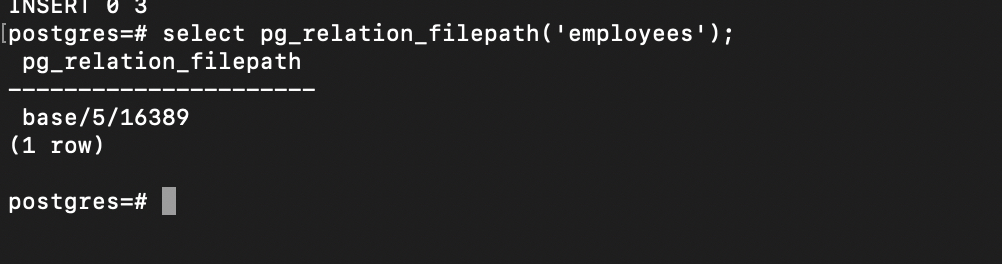
if we go to this folder which located in data directory and run the below command on it the output will come unredable since its encrypted and this showcase the power of pgee tde encryption
head -c 64 base/16388/16394 > sample.bin
hexdump -C sample.bin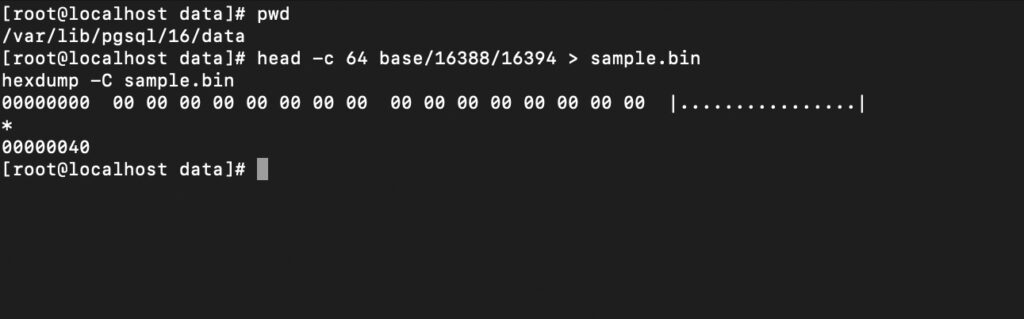
PGEE Data Masking demo
PGEE also comes with powerful built-in Data Masking that is both simple and effective. With this feature, you can mask sensitive columns in a table and then generate a masked dump that can safely be loaded into development or testing environments. This makes it easy to comply with the Saudi PDPL, which requires that any personal data in non-production environments must be anonymized or masked to match production data without exposing real identities.
Since we have create sample table we will mask the name column and then take masked pg_dump and load it to another postgreSQl server
ALTER TABLE employees ALTER COLUMN name SET MASK md5(name);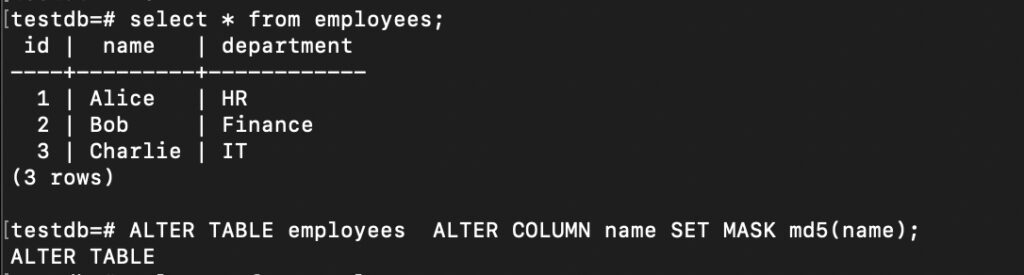
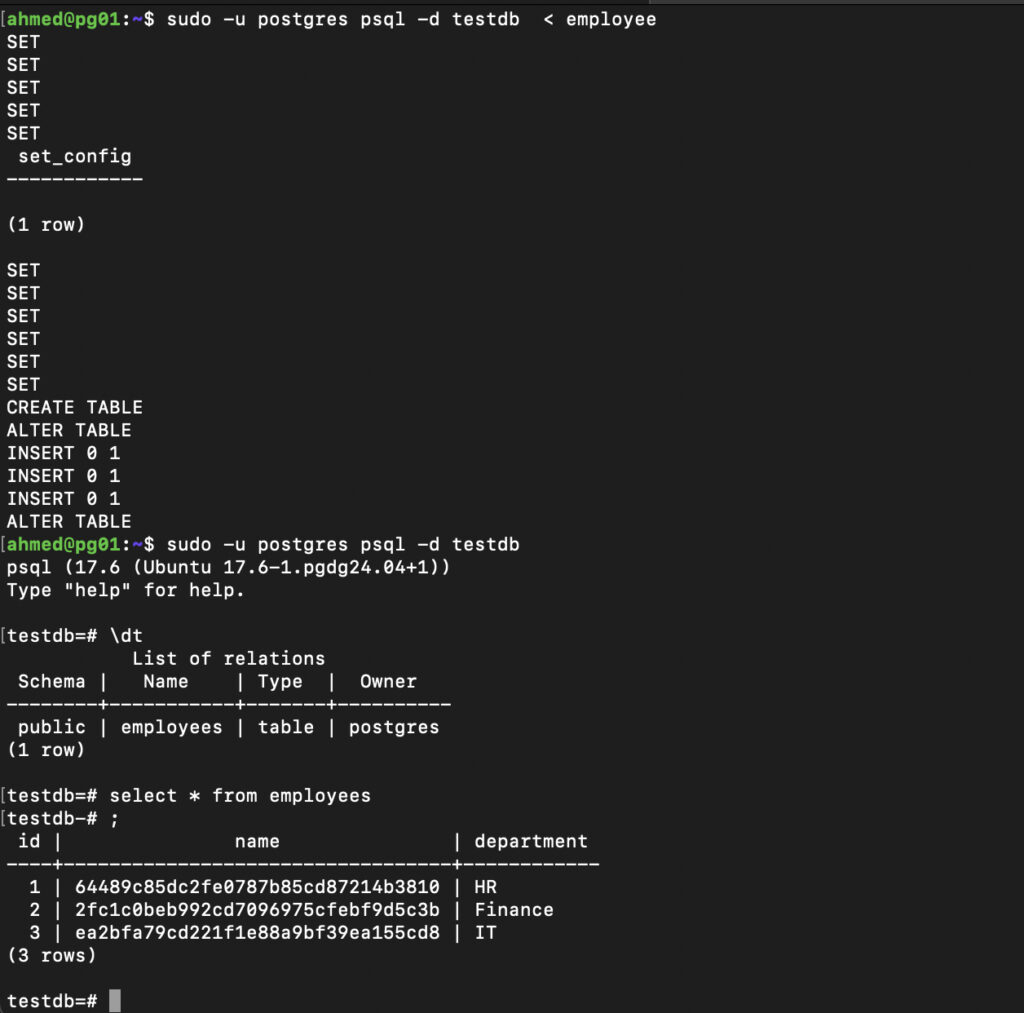
take dump make sure to add option –masked in the command
sudo -u postgres pg_dump --masked testdb --inserts -f employeenow we will restore the backup to different postgresql and when we try to query the table we can see that column masked now show random hash
Hardening checklist (PDPL-friendly defaults you should enforce)
At rest & key management
- TDE is on (see above). In prod, fetch keys via pgee_key_manager or your KMS; don’t echo keys in scripts.
In transit
- Enable TLS and require it:
ssl = oninpostgresql.conf; install server cert/key; usehostsslentries inpg_hba.conf.- Block
host(non-TLS) access paths inpg_hba.conf. (General PostgreSQL practice.)
Auth & roles
- Set
password_encryption = scram-sha-256; disabletrustafter init; enforce least-privilege roles; no day-to-daySUPERUSER.
Network scope
- Restrict
pg_hba.confto CIDRs you actually use (no0.0.0.0/0). Use separate roles per app/service.
Auditing
- Enable PGEE’s enterprise-class auditing and centralize logs with retention (write-once if possible). Review regularly.
Data masking
- Mask or obfuscate personal data in non-prod; limit who can see real values. Use PGEE’s masking policies.
Backups & replication
- Use encrypted backups and encrypted replication channels. Test restores monthly.
Procedures & records (PDPL)
- Maintain records of processing and retention schedules; document where data resides and who can access it.
- Breach playbook: drill your IR plan and wire a 72-hour notification workflow to SDAIA (and notify data subjects without undue delay if risk exists).
Ready to deploy PGEE?
Worlber is an official CYBERTEC PGEE partner in Saudi Arabia. Our local team brings up to 10 years of hands-on experience across finance, government, telecom, and e-commerce. We provide full PGEE licensing plus turnkey setups—HA, DR, or HA/DR—with TDE, auditing, masking, secure replication, monitoring, and runbooks.
- Email: contactus@worlber.com
- Book a 30-min kickoff with our technical team: https://calendly.com/contactus-worlber/30min
